Attackers are getting more slick in launching their email-based threats. Among various threats, clone phishing is one of the most deceptive.
Nowadays, an email from a familiar contact with an almost perfect copy is not always reliable; it may be those attackers who are meant to trick you into giving away your credentials.
Ever wondered how these digital predators manage to fool even the savviest internet users? Protect yourself before it’s too late—read on to find out how this cybersecurity threat works and how to avoid it!
What is Clone Phishing?

Clone phishing is a type of email-based phishing attack in which attackers replicate a legitimate email or website you recognize.
Often, the fake email arrives as a follow-up to an earlier (legit) email, making it even more convincing. It also contains a similar attachment to the legit one; the difference is that the fake email’s attachment contains malware.
Unlike standard phishing, clone phishing takes advantage of your trust in familiar sources to share sensitive information.
How Clone Phishing Works

In Q1 2021, the Anti-Phishing Working Group reported a surge in clone phishing from 9% to 14% of all phishing attacks. This rise may stem from attackers’ ability to create convincing replicas of legitimate websites and emails, which are facilitated by readily available tools and services.
So, how exactly does this attack work? Let’s explore it by reading this explanation:
- Duplication: Cybercriminals create an exact copy of a legitimate email or website.
- Distribution: This cloned content is then sent to the target, often disguised as a follow-up to a genuine message. Typically, the emails are not personally targeted at an individual but at a large group, so they usually don’t directly address you as the receiver.
- Deception: The email contains links or attachments that lead you to a fraudulent website with no HTTP prefix or prompt you to download malware.
- Data Theft: Once you provide your information or download the file, hackers reuse your login credentials to log in to your account and gain access to your data.
Clone Phishing vs. Spear Phishing

While both clone and spear phishing have several similarities, their main strategies are distinct.
Clone phishing works by duplicating a legitimate email or website and tricking users into revealing sensitive information. It sends an almost identical email to a previous one that the recipient already trusts, making detection difficult.
However, it’s a numbers game—casting a wide net rather than pinpoint targeting.
In contrast, spear phishing is highly targeted to specific individuals or organizations—typically high-profile users like C-levels, employees, or network administrators—using personal information they’ve gathered about the victim.
This makes the message appear more credible and increases the possibility that the recipient will engage with it.
In short, clone phishing relies on the trust built from previous communications, whereas spear phishing leverages personalized details to manipulate the victim.
Clone Phishing Examples

Customer Support Scams
Attackers act like real customer support by sending user activity emails from one of their registered social media accounts, telling the receiver to log into their account using the attached link.
For instance, X customer support sends you an email with an attached link to protect your account from a “suspicious” login attempt. In fact, the “suspicious” one is these attackers steal your login credentials once you click the link.
Fake Virus Scams
Besides a fake login attempt alert, a fake virus notification is also another common clone phishing scam.
These attackers act like spokespersons from reputable companies like Microsoft or Apple, alerting you that they have found a nonexistent virus on your computer that needs prompt response. Following the fake alert, they will also recommend a fake antivirus software, which is actually the real virus or malware.
Refund Scams
This scam preys on marketplace users by copying a brand’s writing style to craft an email about an eligible refund or a free gift card. Receivers need to input their personal banking account data to get the refund.
As a result, the attackers will use your data to steal money from your bank accounts.
How to Prevent Clone Phishing
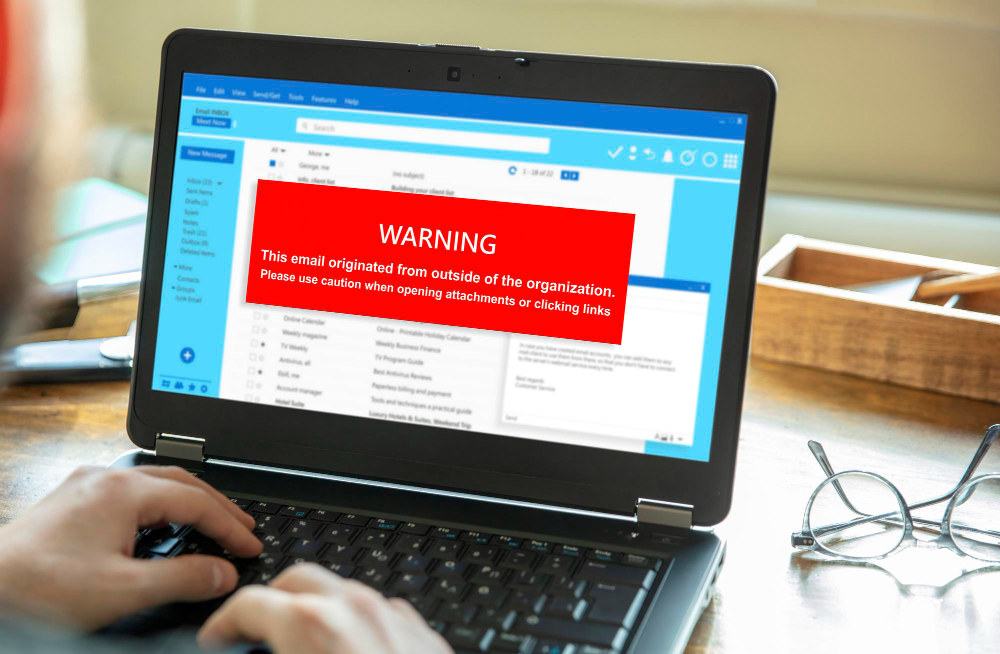
Email Scanning
Utilize advanced email security tools that can detect and block phishing attempts. These tools scrutinize emails for signs of deception, such as suspicious links, unfamiliar sender addresses, or subtle changes in legitimate domains.
Employee Education
Like any other phishing attack, it tricks users into believing that fake emails are real. Regular training is essential to help employees identify phishing attempts. Teach them to inspect unexpected emails carefully and verify the sender before clicking on any attached links or opening attachments.
Threat Mitigation
Develop a comprehensive cybersecurity plan that includes multi-factor authentication, regular software patches, and strong password practices. These measures will help reduce the possibility of falling victim to clone phishing and limit the potential damage if an attack succeeds.
Frequently Asked Questions
What do phishing attacks do?
Has my email address been cloned?
Is cloned and hacked the same thing?
Conclusion
In conclusion, clone phishing is an email-based phishing attack that smoothly impersonates legitimate sources. It is important to stay aware to avoid falling victim. Email scanning, employee education, and threat mitigation are some of the best ways to prevent this attack.
If you want to safeguard your organization’s important data and avoid clone phishing or other types of cybersecurity attacks, reach out to Fluxgate. Our cybersecurity experts will help tailor robust strategies to protect your data. Contact us now!
